WordPress, the world’s most popular content management system (CMS), has found itself in the limelight again for the wrong reasons after an issue which was first discovered back in July 2016 has gone public.
The issue was first reported to the WordPress security team back in July 2016 but until now there hasn’t been a fix or patch for it, hence the public advisory release to aware WordPress users worldwide of the potential vulnerabilities of the hack. The hack affects ALL versions of WordPress, including the latest 4.7.4 version. The vulnerability lies in the way WordPress processes the password reset request. In general, when a user requests to reset his/her password through forgot password option, WordPress immediately generates a unique secret code and sends it to user’s email ID already stored in the database.
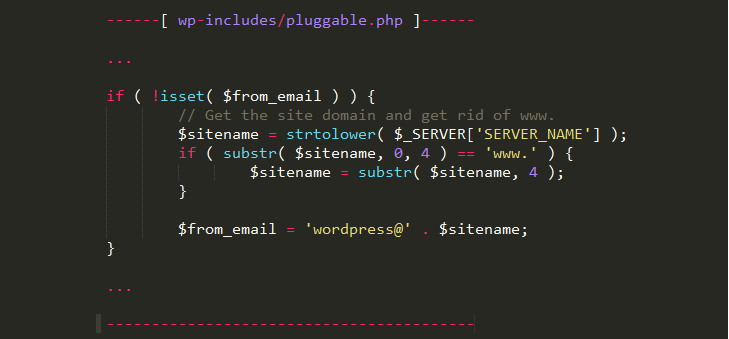
While sending this email, WordPress uses a variable called SERVER_NAME to obtain the hostname of a server to set values of the From/Return-Path fields. Here, “From” refers to the email address of the sender and “Return-Path” refers to the email address where ‘bounce-back’ emails should be delivered in the case of failure in the delivery for some reason. The vulnerability lies where the attacker has the ability to spoof a HTTP request with a custom hostname value (eg. attacker-attacker.com) while it proceeds to process the user’s password request.
Since the hostname can be customised by the attacker, the ‘From’ and ‘Return-Path’ fields can also be manipulated and therefore when the user receives their new password, so does the attacker at the same time. SERVER_NAME server header can be manipulated on default configurations of Apache Web server (most common WordPress deployment) via HOST header of an HTTP request. In other words now that the vulnerability has been publicly disclosed, WordPress admins are advised to take precautions with resetting passwords and in general to be cautious with user credentials.