WannaCrypt (or WannaCry, WanaCrypt0r 2.0, Wanna Decryptor or similar) is a ransomware program targeting Microsoft Windows. On Friday, 12 May 2017, a large cyber-attack was launched, infecting over 230,000 computers in 150 countries, demanding bitcoin ransom payments in 28 languages. The attack has been described by Europol as unprecedented in scale.
The malware is delivered as a Trojan through a loaded hyperlink that can be accidentally opened by a victim through an email, advert on a webpage or a Dropbox link. Once it has been activated, the program spreads through the computer and locks all the files with the same encryption used for instant messages. Once the files have been encrypted it deletes the originals and delivers a ransom note in the form of a readme file. It also changes the victim’s wallpaper to a message demanding payment to return the files.
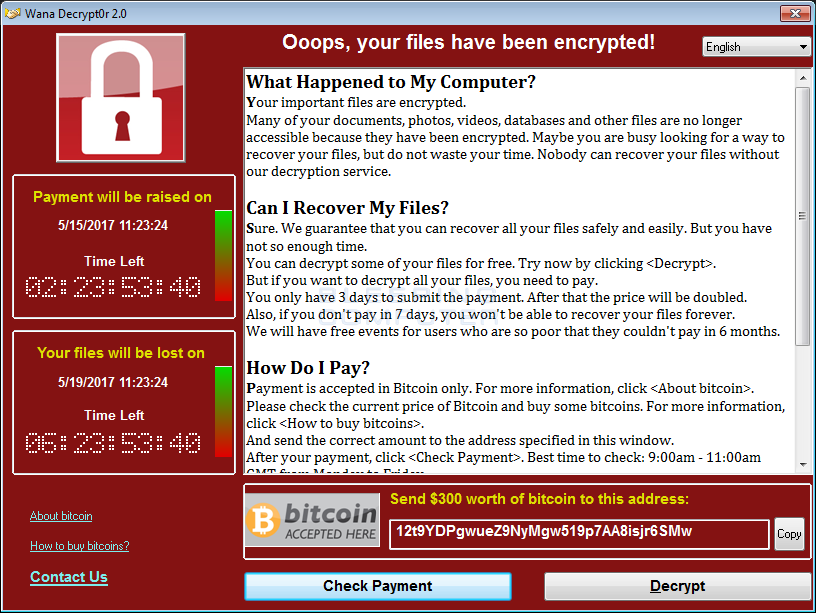
WannaCrypt (or WannaCry, WanaCrypt0r 2.0, Wanna Decryptor) ransom message
WannaCry is believed to use the EternalBlue exploit, which was developed by the U.S. National Security Agency (NSA) to attack computers running Microsoft Windows operating systems. Although a Microsoft patch to remove the underlying vulnerability had been issued on 14 March 2017, users who delayed in applying security updates, or use unsupported versions of Windows, were left vulnerable. Microsoft has taken the unusual step of releasing updates for the unsupported Windows XP and Windows Server 2003 and patches for Windows 8 operating systems.
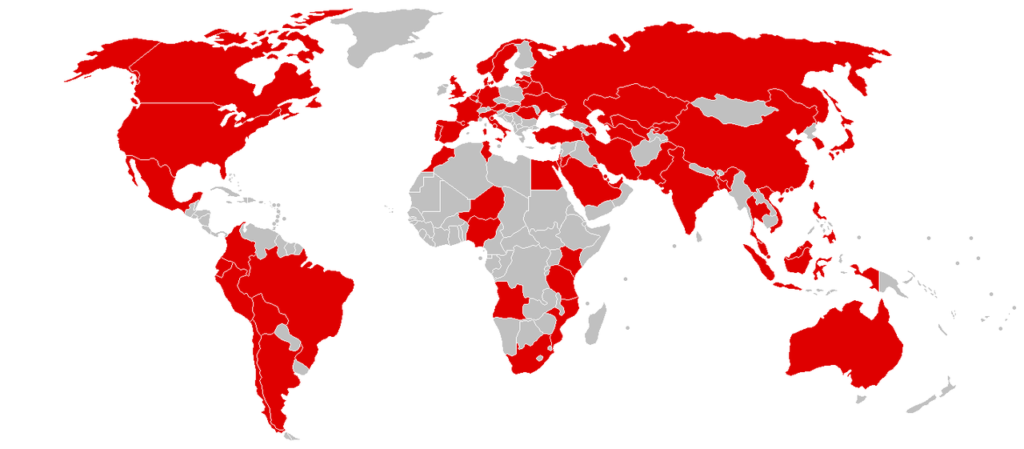
WannaCrypt (or WannaCry, WanaCrypt0r 2.0, Wanna Decryptor) affected 150 countries
On 12 May 2017, WannaCry began affecting computers worldwide. The initial infection might have been either through a vulnerability in the network defenses or a very well-crafted spear phishing attack. When executed, the malware first checks the “kill switch” website. If it is not found, then the ransomware encrypts the computer’s hard disk drive, then attempts to exploit the vulnerability to spread out to random computers on the Internet, and “laterally” to computers on the same Local Area Network (LAN). As with other modern ransomware, the payload displays a message informing the user that files have been encrypted, and demands a payment of $300 in bitcoin within three days – which has reported to be doubled should the time period elapse.
The ransomware campaign was unprecedented in scale according to Europol. The attack affected many National Health Service hospitals in the UK, and up to 70,000 devices – including computers, MRI scanners, blood-storage refrigerators and theatre equipment – may have been affected.
List of affected organisations:
- São Paulo Court of Justice (Brazil)
- Vivo (Telefônica Brasil) (Brazil)
- Lakeridge Health (Canada)
- PetroChina (China)
- Public Security Bureaus (China)
- Sun Yat-sen University (China)
- Instituto Nacional de Salud (Colombia)
- Renault (France)
- Deutsche Bahn (Germany)
- Telenor Hungary (Hungary)
- Andhra Pradesh Police (India)
- Dharmais Hospital (Indonesia)
- Harapan Kita Hospital (Indonesia)
- Cement corporation office (Iran)
- University of Milano-Bicocca (Italy)
- Q-Park (The Netherlands)
- Portugal Telecom (Portugal)
- Automobile Dacia (Romania)
- Ministry of Foreign Affairs (Romania)
- MegaFon (Russia)
- Ministry of Internal Affairs (Russia)
- Russian Railways (Russia)
- Banco Bilbao Vizcaya Argentaria (Spain)
- Telefónica (Spain)
- Sandvik (Sweden)
- Garena Blade and Soul (Thailand)
- National Health Service (United Kingdom)
- Nissan UK (United Kingdom)
- FedEx (United States)
Microsoft ensured that they understood the attack and were taking all possible actions to protect customers. Additionally, Microsoft are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.
Microsoft also said that customers running Windows 10 were not targeted by the attack.
In March, Microsoft released a security update which addresses the vulnerability that these attacks are exploiting. Those who have Windows Update enabled are protected against attacks on this vulnerability. For customers using Windows Defender, Microsoft released an update which detects the threat as Ransom:Win32/WannaCrypt. As an additional “defense-in-depth” measure, keep up-to-date anti-malware software installed on your machines. This attack type may evolve over time, so any additional defense-in-depth strategies will provide additional protections.
Some of the observed attacks use common phishing tactics including malicious attachments. Customers should use vigilance when opening documents from untrusted or unknown sources. IntelliTeK are continually monitoring and updating to protect against these kinds of threats including Ransom:Win32/WannaCrypt. Some antivirus software is capable of catching the WannaCrypt ransomware but there is currently no public decryption (crack code) available. This malware modifies files in the /Windows and /windows/system32 directories and enumerates other users on the network to infect. Both of these actions require administrative privileges.
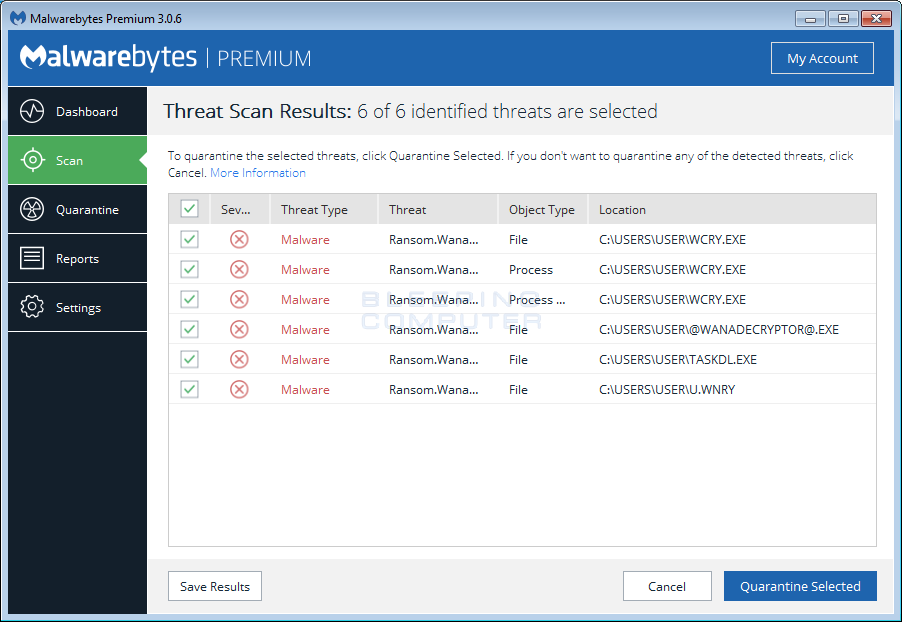
Malwarebytes is one of the antivirus providers that detects WannaCry/WannaCrypt/WanaCrypt0r 2.0/Wanna Decryptor
What To Do:
- Be careful to click on harmful links in your emails.
- Be wary of visiting unsafe or unreliable sites.
- Never click on a link that you do not trust on a web page or access to Facebook or messaging applications.
- If you receive a message from your friend with a link, ask him before opening the link to confirm, (infected machines send random messages with links).
- Keep your files backed up regularly and periodically.
- Be aware of fraudulent e-mail messages that use names similar to popular services such as PayePal instead of PayPal or use popular service names without commas or excessive characters.
- Use anti virus andAlways be updated.
- Use Windows Update to update windows to close the gap.
- Get in touch with us if you suspect something out of the ordinary
With today being the beginning of the work week, it’s still early days and it’s only a matter of time before we find out the real extent of the damage caused by the WannaCrypt ransomware virus. As of writing we haven’t heard much destruction coming from Australian shores as of yet but we have to presume that the attacks targeted every country in the world and that they will most likely spy a weakness in any computer, in any country, including Australia.
IntelliTeK are one of the fastest growing IT service providers that you will find on any list of managed service providers in Australia. We are always up to date with the latest threats to emails and IT security which is why we only partner with the best in the industry. If your company isn’t fully equipped to fend off cyber criminals, then get in touch with us so we can discuss your options. Call us on 1300 768 779, email us at info@intellitek.com.au, fill out the web form, or have a Live Chat with us below.

