Microsoft Office 365 is the fastest growing cloud productivity application and if your business hasn't upgraded to it yet, IntelliTeK can help you install, migrate and manage your personalised Office 365 package. Here are 6 reasons why your business should upgrade to...
Latest News
6 sneaky techniques criminal hackers use
As the years go by criminals take advantage of technological advances and use it for their own methods of attack. Even the simplest things that we take for granted can be used against us. Here are 6 sneaky techniques that attackers may use to attack with: ...
Choosing The Right MSP For Small Businesses in Sydney
Online security issues in Australia are at an all time high so choosing the best managed IT services team for your Sydney business is paramount. The ACCC (Australian Competition and Consumer Commission) reported a billion dollars in losses last year, due to internet...
Managed IT Services Company, IntelliTeK, is a NSW Government Approved ICT Supplier
IntelliTeK has taken the steps to become a NSW government approved ICT supplier and by doing so means that NSW government agencies can find and procure goods and services directly from IntelliTeK. Below are some of the services that IntelliTeK is now registered to...
10ZIG Thin Client Solutions – IntelliTeK are 10ZIG’s sole distributor in the APAC region!
What are the benefits of Thin Clients? Lower Operational Costs - In an office environment where there are multiple workstations, a thin client setup would definitely equal to lower operational costs especially with all workstations being connected to a single server...
IT Services Predictions – Ransomware to subside in the 2nd half of 2017
The IT services security industry and international law enforcement have joined forces to actively detect and respond to ransomware cases around the world. This is one of the reasons why we believe ransomware will subside in the latter half of this year. The IT...
IT Services Study: CEOs Are Cybercriminals’ Number 1 Target
Cyber criminals imitate the CEO and persuade fellow employees to make an unapproved financial transaction - which goes straight into the pockets of cyber criminals. How do they do it? With very little difficulty. Sometimes you can spend billions of dollars on IT...
The Latest In Ransomware Tricks and Predictions
Ransomware creators have a number of clever tricks up their sleeves to make sure that they go about their business unnoticed and make it difficult to undo their work. Let's take a look at some of their methods. Name Encryption One of the more latest ransomware...
Malware 101
The term malware seems to be making the headlines more frequently these days especially with all the cyber attacks on banks worldwide and businesses on a whole here in Australia. But in order to fully protect your business from the threat of malware it is important to...
Need managed IT services in the Gold Coast area?
Originally based in North Sydney, IntelliTeK are no strangers to acquiring and serving clients Australia-wide. With clients as far out as Alice Springs, IntelliTeK have no issues with providing the best managed IT services to companies and organisations in the Gold...
What Happened When An Organisation Refused To Pay The Ransom
A water company in Arkansas, United States found themselves to be victims of a ransomware attack which encrypted 90,000 files on their server and took only under 2 minutes for it to be completed. Their local managed services provider insisted not to pay the ransom and...
Cloud Computing Begins With Hybrid Cloud Services
Hybrid cloud is an environment which has both private and public cloud services, and this is where public cloud resources are easily consumed and integrated into the day-to-day operations of an organisation. It is safe to say most companies will use a combination of...
‘Nigerian Princes’ snatch billions via fake emails
An Interpol-Trend study found that between October 2013 and May 2016, scammers walked off with more than US$3bn having exploited fake email techniques globally. Their techniques, which are no secret on Aussie shores, have slowly evolved from 'send money' emails back...
Managed Services Tips: 5 online habits that you need to give up
Register for this website here. Login to that account there. The online world which we rely on has etched itself into our daily lives, and it has gotten to a point where we can't progress without it. But as with everything in life you can't get too complacent,...
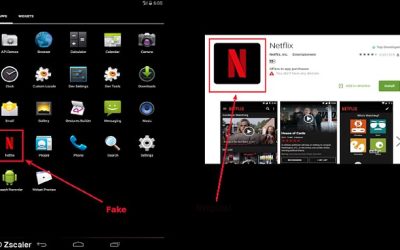
Don’t get caught Netflix & Chillin’ with this fake app
A fake Netflix app has been discovered by cyber-security experts, which can take over your device and spy on you. The device gives strangers access to your phone's camera, microphone and messages so they have access to your life - potentially allowing them to take...
Be wary of wearables – Managed IT Services Sydney
Global spending on managed IT services, particularly in the area of security, is projected to go as high as $350 million this year, more than a 23% increase from last year’s $281.5 million spent in the global market. In the latest study in the managed IT and security...
Latest Managed IT Services Related News For Sydney Businesses
An increasing number of small to medium sized enterprises have been choosing to employ managed IT services in Sydney since it is a cost effective and worry free option. More and more bigger corporations are exercising good judgment and choosing managed IT services for...
Updates For Businesses With Managed IT Support in Sydney
Small to medium sized businesses today are able to compete with global brands, thanks to the world wide web, but cyber criminals are unfortunately targeting these small to medium sized enterprises that is why it is essential to have managed IT support services for...
Managed IT Ransomware Defence Checklist
It's easy to get your business any managed IT service provider and let them handle all your IT security for you but not all are willing to detail the steps that they will take to defend your business from cyber attacks. Here's an IntelliTeK checklist to effectively...
Why We Believe In Amazon Web Services (AWS)
Even though Amazon Web Services (AWS) hasn't been in the spotlight as much as its competitors, we here at IntelliTeK are firm believers that AWS is great for building a business from the bottom as it provides all the tools necessary for companies to start up with the...
Global Banks Under Attack From New Malware
Watering hole attacks attempt to infect more than 100 organisations in 31 different countries in a new wave of attacks which has been underway since at least October 2016. The attackers used compromised websites or “watering holes” to infect pre-selected targets with...
Managed IT Services: Your Small Business Is Vulnerable
An increasing number of ransomware and cyber attacks target small businesses and startups, with ransoms ranging from from a hundred of dollars to 6-figure thousands of dollars - although there have been reports of ransoms going as high as millions for larger...
Yahoo Issues New Email Hack Warning
Yahoo's newly issued warning to users about malicious hacks is related to a third data breach that the company disclosed in December 2016. A warning sent to some Yahoo users Wednesday read: "Based on the ongoing investigation, we believe a forged cookie may have been...
1.5M Unpatched WordPress Sites Exposed to Severe Content Injection Vulnerability
WordPress is one of the most used content management system (CMS) in the world. So when there is a security flaw in its system, it affects millions of users on the Internet. Attackers have taken a liking to a content-injection vulnerability disclosed last week and...
5 Signs It’s Time To Get Your Business A Managed IT Services Provider
According to a 2016 Ponemon study, 69 percent of SMBs don’t have the adequate budget or in-house expertise to achieve a strong cyber security position. As a matter of fact, more than half of the study’s SMB respondents experienced a data breach or cyber attack in the...
Quick Defence Tips Against Business Process Compromise
Business Process Compromise (BPC) is a type of attack that has come into focus recently. It particularly targets the unique processes or machines facilitating these processes to quietly manipulate them for the attacker’s benefit. Attackers infiltrate the enterprise...
Android Ransomware – An old but effective technique
Android.Lockdroid.E is spread via 3rd party app stores as well as doing the rounds on various text/SMS (URLs) messages and forum posts. It targets primarily rooted devices and attempts to drop a version of itself on the rooted device. or if the device is not rooted it...
Citibank Fraud A Nightmare For Managed IT Services Providers
We've seen them before and they come in all shapes and sizes - now they are impersonating Citibank customer emails to make it seem as if you've been locked out of your online banking account, making you enter your login credentials. The elaborate scam involves sending...
Can My Small Business Afford Managed IT Services?
Managed IT is substantially a proactive outlook in dealing with your business computers and IT concerns. IT solutions before now, and it still is in some cases, was mainly on a reactive approach where IT professionals are contacted and brought in when something...
All about Managed Security: IT Services in Sydney
Do you need help managing your IT services in Sydney? More and more companies are outsourcing their IT needs to managed IT service providers so they can focus on growing their business rather than focusing on the technical stuff. A managed IT service Sydney provider...
Why IntelliTeK can be your IT support company in Brisbane
Just because you're located in Brisbane, doesn't mean you have to acquire an IT support company in Brisbane too. The world we are living in means clients, customers and the general service offering can be managed and controlled from anywhere, thanks to 24/7 remote IT...
Make these 5 tips your cybersecurity habits
As better technology rolls out on a daily basis, hackers have equally become more sophisticated with their ways of infiltrating their victims defences. Here's five quick tips which should point you in the safer direction. Enable 2FA 2FA or Two-factor authentication is...
Managed IT Services 101: Data Migrations
A Data migration is the process of moving data between computers, servers, networks or storage devices. Data migration is categorized as storage migration, database migration, application migration and business process migration. These scenarios are routine IT...
New Cybersecurity Survey Reveals Key Managed IT Service Perspectives
IntelliTeK's partner, Watchguard Technologies, have recently released the results of a survey which reveals what managed IT companies in Sydney and nationwide reveal as their top threats to customers, as well as their customers’ ability to manage security alerts and...
Managed IT Services Nightmare: The Malicious Click
Picture the scenario, it's a Friday and you've just got back from lunch, so you open your inbox and see that someone has updated a document in one of the Dropbox folders. You click on the button in the email which takes you to your Dropbox space - but what a minute,...
Fake news sites are bad for our society, and for our computers
2016 saw the highest amount of reported fake news stories on record. The issue of fake stories hit the political scene lately when the WA Liberal Party urged supporters to report “untrue” social media posts by the Labor opposition. “If you see a fake or misleading...
The Role of Managed IT Support in Day to Day Operations
For every business entity, prime results and quality work performance are the main priorities to ensure standards are kept and your company goes to the top of your league. But to do that, you must have your focus and attention dedicated to the centre of your business...
Why Businesses Are Turning To Managed Service Providers
Managed Service Providers (MSPs) have increasingly been sought after to handle all things IT related for businesses who wish to outsource or collaborate with external IT partners. A pattern has emerged during recent times which has seen businesses opt to outsource...
5 Reasons Why You Should Leave Your IT Support Company
Often, business partnerships are like some relationships, good in the beginning but struggle as time goes by. The same can apply for IT support companies who are called upon to provide a service for businesses where unfortunately the negatives are magnified more than...
5 Mobile Malware Threats That You Should Look Out For
Sometimes swiping left or right maybe an ugly option. But swiping right may lead to undesirable consequences due to the simple fact of being fooled by downloading and using fake apps which may leave your private videos and photos being leaked all over the Internet....
4 Reasons Why Outsourcing IT Services Works Best for Today’s SMEs
Running a business entails a lot of resources and critical decision making. Compared to large corporations, it is even more challenging for small to mid-sized enterprises (SMEs) to find ways to get ahead of the competition given the limited resources at their...
What To Expect From A Brisbane Managed IT Services Provider
You and your enterprise may have encountered technical concerns that have led you to decide that you need the help of a managed IT services provider for your Brisbane business. IT managed services providers in Brisbane offer various services and packages but here are...
Managed IT Support Tips: Avoiding Ransomware
Be wary of emails containing invoices that are masquerading under a Microsoft Word document file because it may contain ransomware. Having a managed IT support team that can help filter emails can make a world of difference in trying to keep your business data safe...
Why Hire A Managed IT Service Provider For Your Brisbane Start-up Business?
Most start-up businesses today rely heavily on information technology which can lead to significant time consuming efforts and expenditures. Wouldn’t you rather be focusing on the core functions of your business than trying to understand all the complexities of...
A Good IT Solution: Virtualization and its Role in Business
Virtualization is progressively becoming one of the most integral business IT solutions for companies everywhere. It is quickly taking over half of all server workloads, streamlining software solutions, freeing up valuable resources and significantly reducing...
Why Small to Medium Businesses (SMBs) Need Managed IT Services
Whether you run a small or medium sized business, technology will always play a major role on productivity, efficiency and especially these days, communications. To ensure that every aspect of your business runs as smoothly as possible, you have to stay on top of...
6 Digital Threats During The Christmas Period
It's that time of the year again, and more and more people than ever are buying gifts and presents online than by traditional methods. Let's face it, unless you're buying food, who doesn't want to do their Christmas shopping online from the comfort of their own homes...
Ransomware: Past, Present and Future
For more than a decade, ransomware has been doing the rounds and targeting computer users to an almost personal level. But now ransomware is becoming a huge problem for businesses of all sizes, regardless of industry. Designed for financial gain, ransomware is an...
2016: The Year Of The Hacks
Ranging from data breaches, personal identifiable inforation (PII) theft and alleged hacking of party officials during the US elections, 2016 saw a vast number of cyber attacks. We look back at them and see how those attacks will play out in 2017. Personal Device...
Cloud Computing – Why Your Business Needs To Embrace It Today
More and more Australian businesses have been embracing Cloud Computing and it is forecasted to reach the $790 million mark by 2020. By moving to the Cloud, it doesn’t mean you have to move all of your work-load and be 100% dependent on the Cloud (Well, you can). It...