Proportion of spam in email traffic The share of spam in email traffic in 2017 fell by 1.68% to 56.63%. Sources of spam by country In 2017, the US remained the biggest source of spam (13.21%). A 6.59% hike in spam distribution pushed China up to second place (11.25%)....
Latest News
Spam and Phishing – Part 2 of 3
Phishing pages migrate to HTTPS Sites have been moving to HTTPS in increasing numbers, and not just legitimate resources. If a year ago a top tip for users was “check that pages requesting personal data are secure,” today a certificate does not guarantee safety:...
Spam & Phishing in 2017 – Part 1
Figures of the year The share of spam in mail traffic came to 56.63%, down 1.68% against 2016. The biggest source of spam remains the US (13.21%). 40% of spam emails were less than 2 KB in size. The most common malware family found in mail traffic was...
The Weakest Link In Data Protection – The Human Factor
A company's greatest asset - it's employees - can also be its weakest link, especially in an era wherein mobility and accessibility play a huge role in enhancing productivity. Employee negligence puts an organisation in risk 78% of organisations have suffered from at...
Bee Token falls victim to cyber criminals; nearly $1-million lost
Cryptocurrency startup Bee Token confirmed that scammers conned its investors out of at least $928,000 worth of ethereum when it ran its initial coin offering (ICO). The fraudsters who phished the investors posed as the Bee Token team, urging them to quickly...
Cyber attack hits the 2018 Winter Olympics; attack played down by officials
Pyeongchang Winter Olympics organizers confirmed on Sunday that the Games had fallen victim to a cyber attack during Friday’s opening ceremony, but they refused to reveal the source. The Games’ systems, including the internet and television services, were affected by...
The Current State Of Ransomware – Prevention and Detection
One of the recent examples of such an attack is Bad Rabbit ransomware that hit Ukraine and Russia in late October of 2017. Based on the well-known EternalBlue exploit, it targeted old Windows systems that weren’t properly updated. While the exploit itself has already...
Don’t over-complicate or get complacent with your passwords
Passwords are everywhere. From logging in to our social media accounts to buying new shoes, we wouldn’t be able to get much done without first logging in to an account with a password. The problem is, as more and more of our everyday lives have gone online, we’ve had...
How we should accept digital extortion into our lives
Digital extortion has evolved into the most successful criminal business model in the current threat landscape, and Trend Micro researchers predict that it will continue to grow rampant because it’s cheap, easy to commit, and many times the victims pay. The line...
Booking a holiday online anytime soon? You might want to read this first
The travel and hospitality industry suffers billions of losses each year due to fraud. With the right combination of other underground services (compromised accounts, credit cards, etc.) it is possible to cover almost every aspect of the holidays, including food and...
Traditional managed IT services vs. The Cloud
For more than a decade now, cloud computing has been causing massive changes in IT. It’s all about the agile and nimble way of doing things compared to more traditional IT models. What’s changed exactly? Here are a few areas of IT that have been upended by the cloud...
The relationship between managed IT services and the cloud
The ecosystem around the cloud is growing and changing rapidly, and most of the executives are (re)considering who they partner with and what they partner for to accelerate the value technology brings to their organizations. Managed IT Services is an area that has...
What should you do if you’ve fallen victim to a data breach?
With online activity on the increase from managing your banking accounts to shopping online, your data is stored on servers around the world and are prime targets for cyber criminals. Sometimes by the time you've found out that you've been compromised it maybe too...
4 Cyber security tips for 2018 – Don’t get left in 2017
2018 is the year to learn from 2017's security mistakes. Securing yourself online will only be as good as your practice of it. Modern day cyber security is known to be more innovative and arguably more successful as the years go by. There should be a check list which...
The Global Managed IT Services market hit US$149-Billion in 2016
Figures from ReportLinker states the global market for managed IT services reached US$149.1 billion in 2016 and is estimated to reach US$256.5 billion in 2021 from US$166.7 billion in 2017. An increase in digitization, mostly from cloud based services from the...
CPA Australia Imitated By Cyber Criminals, Attempts To Hijack Your PC
One of the first cyber attacks to hit 2018 is the email phishing scam using CPA Australia's identity. Following previous styles of attack, emails are sent to dupe recipients into thinking that it is legitimate email from the company when in fact it's intended purpose...
New Year, Same Android Vulnerabilities – Bypass Flaw Found in Samsung Devices
The vulnerability, Same Origin Policy (SOP), comes pre-installed on millions of Samsung Android devices worldwide and allows attackers to steal data from the Samsung Internet browser. Identified as CVE-2017-17692, the vulnerability bypass issue resides in the popular...
Cloud Wars – Cloud Computing Predictions for 2018
What can we all expect for the year ahead when it comes to the cloud? Managed IT experts and leaders have their say. One thing's for sure, the cloud industry certainly is going to stay static, rather it will continue to innovate and change at rapid pace. Hybrid Cloud...
The time to invest in Managed IT services is NOW
CompTIA, the world’s leading tech association, recently released a report about the annual trends in the managed services industry. After analysing its findings, here is a concise argument as to why you should invest in managed IT services, particularly in Sydney. The...
Windows 10 users at risk of getting their passwords hacked
In yet another alarming security nightmare for managed IT service providers in Sydney, a recent blog in the Chromium revealed how Windows 10 users may be at risk of having all their usernames and passwords hacked. Here is everything you need to know about this...
IT services block scam attack: CityLink brandjacked!
Managed IT service providers were once again able to block fraudulent emails to Sydney users. As the holiday season draws nearer and nearer, the scams are becoming more and more prevalent as well. Thankfully, those who are protected by managed IT experts were able to...
Users beware: Malicious apps found in Google Play Store
Many people are lax about their mobile security, downloading apps left and right with no worry about the consequences, since these apps should have been regulated by the publishers. Yet as managed IT service providers know, users in Sydney and all over the world...
Cybercriminals hijack Christmas: Scam emails flood Australian inboxes!
By now we are no longer surprised to see how cyber criminals would go the extra mile just to dupe a handful of people out of thousands. The holiday season is always on the list of opportune times to strike, not only for cybercriminals but also for criminals in the...
Managed IT services security update: Largest Bitcoin mining marketplace hacked, $70 million stolen!
The growth of cryptocurrency continues on. The present price of 1 bitcoin is equivalent to $14,800, a staggering amount in all aspects. Just imagine what you can do with one bitcoin alone—with that much money, you will have endless opportunities in this world. This...
Scam alert: Massive phishing scam targets inboxes
Phishing scams are becoming more and more common nowadays. In fact, we almost see a new one every day, with the scams ranging from very obvious to cleverly executed. Yesterday, security expert MailGuard reports that a massive scale phishing scam was launched. It seems...
Google to restrict third-party devs from injecting code into browser
Have you ever experienced your browser crashing in the midst of an important work? This crash may be caused by a third-party application that is injecting code onto your browser. As it turns out, Google is set to restrict this from happening in mid-2018. According to...
Hybrid Cloud vs MultiCloud: What you need to know
The Cloud, a term that refers to Internet-based software and services instead of locally on your computer, is becoming a business necessity today. Using the Cloud protects your investments, secures your data, and enables telecommuting and enhanced flexibility. In...
Telstra tagged by hackers: How to protect yourself from phishing emails
Leading managed IT service providers identify the latest scam from the arsenal of scammers, this time tagging Telstra, one of Australia’s telecommunications and media company. The large scale phishing attack is well executed, containing the usual interface from the...
Scammers are after your login information, too!
Most people think of compromising your credit card information when you are targeted by cyber criminals. However, an even more common scam is one wherein your login credentials are stolen. Read about this latest scam here. There are reports of the new scam that is...
Fast-fashion retailer Forever 21 the latest victim of data breach
While most companies are gearing up for Black Friday sales this week, it seems that one brand will be busy trying to secure its stores and appearing its customers. Fast-fashion retailer Forever 21 disclosed of a possible data breach in a handful of its stores. The...
Criminals brandjack PayPal: Is your account compromised?
PayPal is one of the most trusted payment gateways in the Internet today. However, not even the most trusted brand is safe from cyber criminals. Read about the latest scam to target consumers and IT professionals here. Leading security expert Mailguard recently...
The importance of partnering with your managed IT services provider
Managed service providers (MSPs) are becoming more and more popular in the tech landscape today. Managed IT service providers, in particular, are becoming instrumental to most companies. IntelliTeK, as one of the leading managed IT service providers in Sydney, is here...
Understanding the Cibecs Advantage – Contact IntelliTeK Today!
In a previous blog, we talked about our latest data protection solutions line offered by Cibecs. Here’s everything you need to know about it. Cibecs is considered as the simplest way to backup, protect and secure business endpoint data. It is a South African developed...
How your business will benefit from Cibecs data protection solution
Data protection is an integral part of every business. IntelliTeK, in a bid to provide you with the best solutions available in the market today, has included Cibecs in its portfolio of products. Find out how Cibecs can enhance benefit your business today. What do...
IntelliTeK: Helping you reach your full potential through managed IT services
There are many managed IT services providers in Sydney, yet there are only few companies that can offer you end-to-end processes that safeguards your data and enhances your productivity. IntelliTeK is one of these companies. IntelliTeK, an industry leader in managed...
4 reasons why outsourcing managed IT services is better than in-house IT
As technology trends continue to rise and fall all over the world, many companies across different industries are at a loss as to how to fully harness the technological advances to their advances. As a result of taking matters into their own hands, many of these...
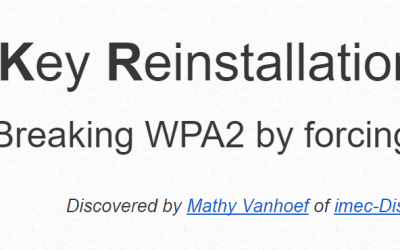
KRACK attacks vulnerable Wi-Fi’s all over Sydney
Most, if not all of us, utilise Wi-Fi networks in our homes and businesses. If you’re using a mobile device, regardless of the brand and operating system, the chances that you are also connecting to a Wi-Fi network is very probable, too. We’re mentioning this to...
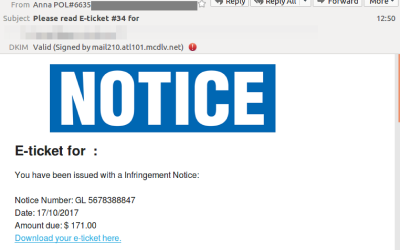
Infringement Notice Scam: Email scam targets Australia inboxes
A new email scam has hit inboxes across Sydney and all over Australia and are bringing IT services experts scrambling. The scam harnesses the urgency of a legitimate issue; in particular, e-ticket infringement notices. An e-ticket is defined by the Queensland Police...
Protect Your Company from These Data Protection Myths
Governments all over the world are cracking down on data protection. Never before has privacy and confidentially been uttered with utmost seriousness in the corporate world. After all, data is the bread and butter of your company. If your data is lost, compromised, or...
Are iOS owners at risk of phishing scam?
Apple sold its billionth iPhone on July 27, 2016, an impressive feat since the brand has been on the shelves for less than 10 years after it was launched on June 29, 2007. It is estimated that at least 700 million iPhones are currently actively being used in the...
Managed IT services nightmare: Security breach affects 17.5 million subs
In the wake of Yahoo’s disclosure that a 2013 data breach affected 3 billion subscribers around the world come this equality terrifying news from Disqus. Disqus, described as a “worldwide blog comment hosting service for websites and online communities that share a...
Another email scam hits Australia
Many companies that offer managed IT services also include impressive security packages for their clients. As the recent spate of phishing attacks in Australia can attest, managed IT in Sydney can improve by a notch or two when it comes to educating users to use...
Flashback Friday – 5 Breakthroughs In Computer Network History
Today we take a look back at some of the amazing advancements in computer networking and how some of them have changed the world and the way we live our lives, forever. The Internet Developed in the late 1960's, the Internet originated from the United States' Advanced...
ANZ Phishing Scam Emails Claim Your Last Payment Was Unsuccessful
So you've received an email this week regarding an unsuccessful transaction on your ANZ bank account? Chances are the email is fake and it is trying to steal your personal credentials. Our friends over at Mailguard have reported a fake phishing scam email originating...
Create Your Own Ransomware Android App Discovered
More bad news for device security as the existence of Android Apps which allow even novice tech users to create their own ransomware has been discovered. What's worse is the app appears to generate ransomware with just a few taps using its friendly UI. The days of...
Be careful who you’re chatting with on Facebook Messenger, malware found
An advanced and potentially malicious Javascript code injector is spreading via Facebook Messenger and it is still unknown as to how it is spreading around. Even though the method is pretty old school it still has the properties of a destructive piece of malware....
Sony PlayStation’s Social Media Compromised, PSN Possibly Hacked
While we hope there aren't any PlayStation Networks accounts hooked up to your office environment, it appears Sony have been compromised by a group claiming to be a 'white hat IT Security' firm. A group of Saudi Arabian hackers calling themselves OurMine posted a few...
8 Google Chrome Extensions Hacked Last Week
Google Chrome, arguably the world's most popular web browser has come under attack last week from hackers who have managed to compromise eight of its extensions which are readily available on the Chrome Web Store. It's believed that hackers compromised one of the...
Security Is The Forefront Of IntelliTeK’s Managed IT Services
IntelliTeK's modern day managed IT services has evolved from providing our clients better, streamlined IT solutions to ensuring our clients are safe from the daily threats of cyber criminals. Almost overnight, cyber security has risen to the top of the agenda when...
We answer a few questions about cyber security and cyber threats
We'll answer some questions about cyber security and provide you with some tips to detect and protect yourselves against online threats. Q: Can regular, non-expert, computer users be trained to handle cyber threats? A: Anyone can be trained to spot the basic of online...
Three mobile ransomware you need to look out for
From file hacking to cryptocurrency stealing to school boy errors, here are three notable mobile ransomware which you should be cautious about. SLocker Largely imitating the Petya ransomware, SLocker combines with the use of the China-based social networking website...
4 reasons why an IT disaster recovery plan is essential for any business
Having an IT disaster recovery plan is an essential business need. People often overlook it because they think that they already have all angles covered or they simply think a 'disaster' won't happen to them. Today in 2017 it's safe to say we are at the peak of cyber...
Another E-Toll phishing scam is hitting our inboxes this week
It seems the cyber criminals have taken a liking to the E-Toll emails as a new phishing email is making the rounds, following on from last month's Road and Maritime Services email scam. Fortunately the latest scam is nothing we haven't seen before and it was easy to...
This Russian mobile banking malware takes over your mobile phone
The "Svpeng" malware has evolved since 2013 and now it has new added functionality to become a keylogger, stealing entered text through the use of accessibility services (Android). On Android, Accessibility Services provides user interface (UI) assistance which aid in...
EnergyAustralia phishing scam emails hitting your inboxes right now
Following similar patterns to previous phishing scams, the emails are designed to trick the recipient into downloading malware. (Credit to MailGuard for the above image) The email looks realistic and to the untrained eye mimics an original email until you look closely...
Top IT Support Issues That You Can (Generally) Fix Yourself
There’s nothing IT support loves more than assisting clients with their tech issues but generally, there are some common issues which you may fix yourself or at least check to make sure that you are indeed doing the right thing. Unable to log in Left the good old Caps...
“Broadpwn” exploit eliminated with iOS 10.3.3 update
This release fixes a serious vulnerability in the Wi-Fi chips used in iPhone, iPad, and iPod touch, which allows an attacker to remotely take control of your device over a wireless network. Like a lot of mobile devices, Apple’s use Broadcom chips for Wi-Fi...
Why managed IT services providers recommend Thin and Zero Clients
Managed IT services providers will almost certainly recommend a setup which allows lightweight computers to replace desktop computers and connect to a server to deliver the software applications that your staff need. Referred to as Desktop Virtualisation, software...
Why should you outsource your IT services?
Small to medium businesses will benefit the most from outsourcing their IT services to a dedicated managed IT services provider. Most businesses are doing so and it continues to be the trend. If you haven't outsourced your IT yet, here are a few points which will...
IT Support News: The Windows 10 Creator Update (RedStone 3)
The much anticipated Windows 10 Creator Update (RedStone 3) is just around corner with it expected to be released around September-October 2017. Also dubbed the "Falls Creator Update" it brings to the table a vast list of improvements to the operating system with a...
New Week, New Ransomware: LeakerLocker steals and shares your data
Downloadable via compromised apps on the Google Play Store, the LeakerLocker ransomware threatens to send all of your pictures, messages and internet browsing history to all of your contacts. Once a compromised app has been downloaded, LeakerLocker locks the phone's...
WatchGuard Security Technologies – #1 Choice for Managed IT Services
We are in the midst of modern day cyber crime where everyone from students to large worldwide organisations are prey for cyber criminal predators. Which is why it's essential that your managed IT services provider offers your business only the best network security...
Fake Android app infects 14 million devices worldwide
Dubbed CopyCat, this malware has already infected 14 million devices and has caused nearly AU$2 million in damages in the space of only two months. Out of the 14 million infected devices, 8 million of them were rooted by the malware, 3.8 million devices were used to...
You may get Malware if you’re interested in the North Korean Missile Program
Last week North Korea claimed that it carried out its first test of an intercontinental ballistic missile (ICBM), the Hwasong-14 and US officials believe the country may have fired a brand-new missile that has not been seen before. No we haven't turned into a...
4 of the most destructive Botnets in recent times
Botnets are underdogs when it comes to cyber security but if orchestrated properly they can cause a world of destruction, as we will go on to talk about later. Firstly, what is a Botnet? A botnet is a when a device which is connected to the internet gets taken over...
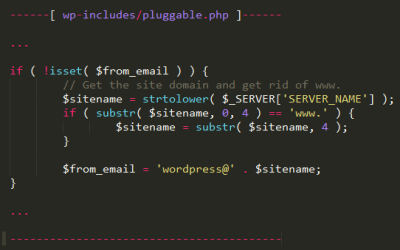
If you’re using this WordPress plugin you might want to update it now
WordPress plugin which has been installed on 300,000+ websites around the world has been found to have a "severe" SQL injection vulnerability. Security firm Sucuri were auditing popular open source projects when they came across the vulnerability in the WordPress...
Make software updates a part of your daily regime
Any managed IT services company will tell you about the importance of updating your software especially when most think of it as a chore. Understandably the update reminders and restarts prompts will come at a wrong time but it is essential that you adhere to them on...
What do hackers do with your personal data?
In 2016 fraud and identity theft resulted in $21 billion worth of losses and was proving to be a lucrative gold mine for cyber criminals. Lucrative because it provided hackers with leverage to negotiate ransoms with businesses, organisations and individuals. In some...
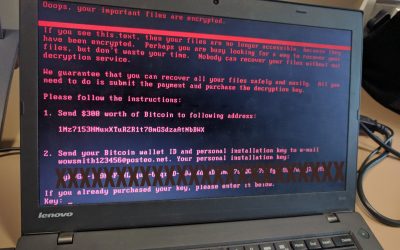
WannaCry Ransomware is still around. Right here in Australia!
Weeks after the WannaCry ransomware shut down hospitals and businesses across the world, there have been reports of it successfully causing havoc in Japan and Australia. The self-spreading ransomware is still alive and kicking and the latest victims are Honda Motor...
Europe Under Fire: New Ransomware Takes Over Europe
There have been reports of a huge cyber attack which has, so far, crippled firms, airports, banks and government departments across Europe. Code-named 'Petya', it is bearing similar resemblences to the WannaCry hack. What do we know so far? Ukraine has bared the...
Managed IT Services 101 – 5 Advantages Of Cloud Backup
In light of recent cyber attacks, the spotlight is now on businesses to ensure that they have the right security in place to protect themselves on a daily basis from hackers who are using more and more sophisticated techniques to infiltrate business defences. One huge...
A company has just paid AU$1.3-Million to Ransomware Hackers
A South Korean web hosting company fell victim to ransomware hackers and had more than 150 of its servers compromised. Hackers demanded an equivalent of AU$5.8-million in ransom, but after a week of negotiations both parties agreed a fee of around AU$1.3-million - to...
IT Services Report: ‘Xavier’ malware on the loose on the Google Play Store
IT Services researchers over at Trend Micro have discovered the malicious 'Xavier' malware which come pre-installed on a wide range of Android apps including photo editors, wallpapers and ringtone changers and phone tracking. There are reports of over 800 Android apps...
Microsoft PowerPoint can present you with malware
A new social engineering attack has been discovered in the wild, which doesn't require users to enable macros; instead it executes malware on a targeted system using PowerShell commands embedded inside a PowerPoint (PPT) file. In the past attackers have been...
Westpac customers it’s your turn to have your account ‘locked’
Cyber attackers have been targeting Westpac customers this week but by the looks of things they didn't put much effort into their attack as the phishing emails appear to be pretty low-tech. Nonetheless let's get into the details of the fake phishing email. It's...
5 Ransomware Defence Pointers For You And Your Business
Ransomware is now the fastest growing class of malicious software and it has evolved from simple screen blockers demanding payment to something far more dangerous. Don't take the authorities' word Don't rely on word from Government agencies saying they have doused...
Roads and Maritime Services email phishing scam doing the rounds
Another week and another fake impersonation email is hitting Australian inboxes nationwide this week. Looks and feels just like the real thing but of course it isn't. Let's see what this scam email is all about. Looking like a wolf in sheeps clothing, emails...
Three Of The Best Malware Fails Of All Time
There have been some malware goofs in the past which are worth talking about. Ranging from the author's identity being revealed to a decryption key being left on an encrypted machine and even some funny malware names. Let's take a look at the three best malware fails...
DocuSign users may want to read this
Electronic signature and digital transaction management firm, DocuSign, reported email address theft on May 15. Despite there being no loss of personal information during the theft, DocuSign say that a malicious third party gained temporary access to a separate,...
New Fake ASIC Emails Unleashed This Week
Yet another wave of scam emails have been hitting inboxes this week, fortunately it appears to be something that we've seen before. The scam carries the same ingredients as previous scams - fake email, fake link and malware. The first reports of the scam were on...
IntelliTeK Pty Ltd – Top Rated Managed Service Providers Sydney
IntelliTeK is a team of IT professionals who have over 60 years of experience in consultancy, managed IT services and software engineering. We actively work in an environment where positivity stems from the bottom, up. We seek to provide solutions to all problems and...
IT Services Sydney – Why Outsource Your IT?
IT Services Sydney is usually taken care of in-house or outsourced to a managed IT services company. After all every company has their own circumstances and one offering may work best for one company, with the other offering working best for another company....
Hacked In Translation: Streaming movies isn’t safe as you think
You're probably asking, but how? Well it's all to do with the subtitle files themselves and since they usually bypass security software it gives the attacks full control of the system. So that was it in a nutshell. But going into detail, a team of researchers at Check...
Here are 10 ways ransomware has most likely tried to attack you
Ransomware has been trending lately with the recent WannaCry outburst. The rate of infection is definitely on the increase due to cyber criminals' illicit methods of attack. READ OUR RELATED ARTICLE: MANAGED IT RANSOMWARE DEFENCE CHECKLIST The 10 methods of attack...
Web Security 101 – How Secure Is Your Home Router
Modern day web security means you have to keep all your senses open and be alert to any potential breaches to your security. Not everybody includes their home router on the top of their web security priority list and since it is often over-looked, cyber criminals have...
Move over WannaCry, there’s a new Ransomware in town
Adylkuzz is a CoinMiner malware, which means that it employs - without user consent - machine resources to mine coins for virtual currencies. It appears to exploit the same vulnerabilities as the WannaCry ransomware did but in a more stealthier fashion. On paper...
Web Security 101 – Top 5 Least Wanted Malware
Here at IntelliTeK we make web security a number one priority and we have come up with a list of the top five least wanted malware and how to defend yourself against them. Firstly, let’s define what Malware is – Malware is an abbreviated term derived from “malicious...
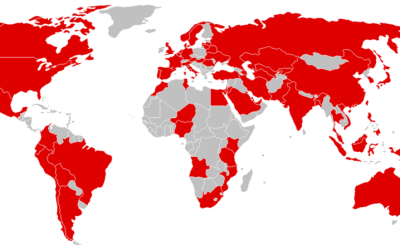
Global disruption of IT services because of ‘Wannacry’ ransomware
IT services around the world are waking up to the aftermath of the 'Wannacry' ransomware malware which hit a majority of countries around the world in such a short amount of time. IT services across the private and public sectors of most countries have been working...
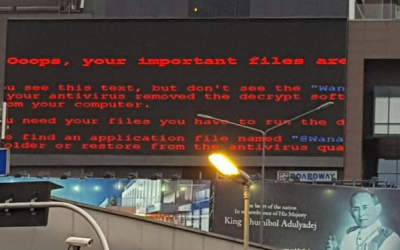
The WannaCrypt Ransomware Attack – Here’s All You Need To Know
WannaCrypt (or WannaCry, WanaCrypt0r 2.0, Wanna Decryptor or similar) is a ransomware program targeting Microsoft Windows. On Friday, 12 May 2017, a large cyber-attack was launched, infecting over 230,000 computers in 150 countries, demanding bitcoin ransom payments...
IntelliTeK – One of the top managed service providers in Australia
When composing a list of managed service providers in Australia you will definitely see IntelliTeK's name as one of the most efficient, most competitive and most reliable especially when it comes to post-sale requests such as technical support and security. Managed...
Don’t waste your time and energy clicking on this fake email
Fake Origin Energy electricity bills have been making the rounds today and as usual they are pretty convincing and contains a direct link to malware. Thousands of fake emails have reportedly landed in people's inboxes today (May 10th 2017) and the emails look like a...
WordPress Admins Warned To Be Cautious About Potential Hack
WordPress, the world’s most popular content management system (CMS), has found itself in the limelight again for the wrong reasons after an issue which was first discovered back in July 2016 has gone public. The issue was first reported to the WordPress security team...
Be Weary Of The New Google Docs Phishing Scam
Google confirmed that they are aware of the scam and have already taken action to protect users against an email impersonating Google Docs by disabling the offending accounts. The phishing scam followed the same ingredients as other phishing scams by using deceptive...
Why Cloud Services Are More Equipped To Fend Off Email Spam
Email filtering is the process involving the segmentation of certain emails by specific criteria. Included in email filtering is spam filtering where unsolicited and unwanted emails are filtered out so that your inbox or even servers do not get clogged up. Cloud...
Here’s Why Microsoft Has A Cloud Data Centre Under The Ocean
Tech companies such as Facebook and Google have their data centres in colder parts of the world due to the heat, but Microsoft has gone one better and decided to drop a Cloud Data Centre under the sea. Microsoft says that 50% of people live near the coast and dropping...
This Impossible Phishing Attack Is Hard To Detect – Managed IT Report
Hackers use a vulnerability in popular web browsers such as Google Chrome, Mozilla Firefox and Opera to spoof the web address bar with 'legitimate looking' web addresses in order to steal login or financial credentials from users. Millions of Internet users who are at...
A Boost For Web Security? Mastercard’s New Fingerprint Scanner Card
After two successful trials in South Africa, Mastercard are rolling out a payment card which features a fingerprint sensor. The cards are thought to be the first to include both the digital template of the user's fingerprint and the sensor required to read their...
IT Services Advisory: Fake Super Mario Run App Steals Your Data
Released in September 2016 on iOS and March 2017 on Android, Super Mario Run looked to follow in the footsteps of popular mobile games such as Pokemon Go and even Candy Crush but as with most apps nowadays attackers have released versions of these fake apps that steal...
Managed IT Services 101 – Think before you click
It is usually the managed IT services company who mops up after a security breach and more often than not the breach originates from users clicking on things that look normal to click on. Let's take bogus MYOB emails as an example, there have been attempts by cyber...
10ZIG Zero Client Solutions – IntelliTeK are 10ZIG’s sole distributor in the APAC region!
Zero Client VDI Solutions consist of the following qualities: Fastest boot-up possible Lowest power-consumption Most secure data Least amount of IT maintenance A nearly completely OS-free VDI experience 4448 Series Zero Client Value Class Thin Client Model Numbers:...